It’s rare to genuinely experience nostalgia towards malware. Despite my persistent efforts over the past week, nothing seems to be falling into place. Are there any illegal uses that are sneaking into the system via shady installers or malicious .exe files? In recent days, I’ve struggled to muster a hint of nostalgia towards these companies, despite their notorious reputation for bogging down computers or inserting unsolicited search bars into elderly parents’ browsers.
They indeed set off without hesitation. After considering the prospect of malware, which I’m convinced still lurks online, awaiting its chance to strike, my thoughts are transported back to the late 1990s. As I reflected on the initial discovery that my seemingly harmless computer had morphed into an ominous portal, capable of siphoning away my hard-earned savings and transferring them to someone else’s bank account with impunity.
A brand-new puzzle game from Odd Games isn’t a lighthearted nudge at players’ memories, but rather a thought-provoking exploration of their recollections. As the digital realm’s fond nod to bygone eras, the system’s email inbox, reminiscent of Windows 95’s, harmoniously coexists alongside an assortment of courteous grey software wizards, inviting exploration through their intuitive interfaces. Don’t be fooled. This is a truly ingenious concept for a horror game. The terror often stems from a fundamental fear of being consumed by something that erodes one’s sense of self.
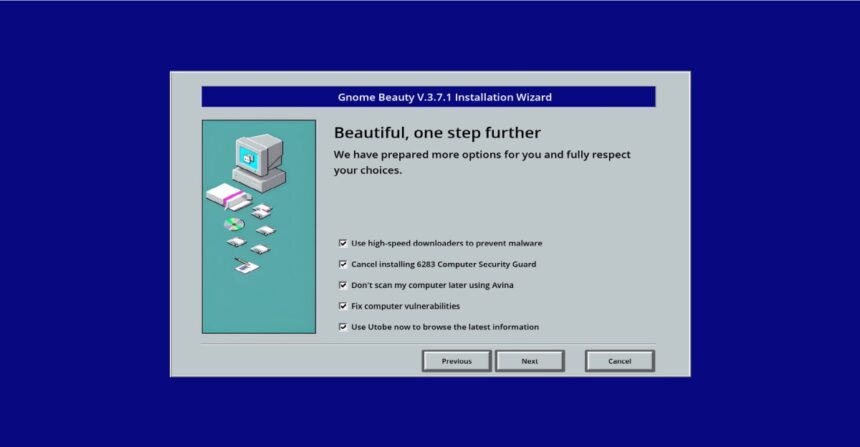
None of this is to say that everything isn’t sort of fantastic, after all. The email exchange often commences with a deluge of messages from frustrated computer users worldwide, each one beset by various technical issues and queries. Regardless of their individual stories, customers are striving to complete the necessary applications without burdening themselves with unnecessary ones attached along the way. Crushed by their previous failures, they’re seeking guidance to turn things around. Each incoming email presents a fresh challenge, with the diverse array of messages serving as nuanced interpretations of a core objective. Launch the program you’ve received, navigate through its diverse examination modules and carefully review the end-user license agreement (EULA). Did you manage to follow through on your plan? How did it go? Were you able to secure the data you were seeking without unnecessary collateral?

Picture: Odd Video games
Precise malware detection requires attention to minute variations, which can be frustratingly inconsistent at times. Early challenges may swiftly recede from view, becoming entangled with seemingly harmless test containers that cunningly conspire to conceal something malicious by cleverly inserting it into a benign-looking list item’s core. Later software updates pose a multitude of frustrations, including buttons with mislabeled options, convoluted language, auto-downloads that must be interrupted, obscure containers buried within license agreements, and a plethora of alternatives that leave users pondering what, exactly, is intended by the choice to opt for a “custom installation”? If you’re seeking a sport that transforms the progress bar into a genuine harbinger of fear, then this is it.
Here is the rewritten text:
The exceptional quality of this judging is undeniable. Nevertheless, I’ve increasingly realized that its effectiveness stems from the same underlying principle that drives malware to function effectively in the real world. Their schemes succeeded because they sensed that even before attempting to deceive me, I felt utterly impotent sitting before the bland authority of a computer screen. This remains accurate even when, upon closer examination, the apparent authority of the window no longer aligns with my understanding of what constitutes legitimate authority.
Computer systems’ complexity is staggering, operating on principles that vastly exceed my comprehension. When they condescend to provide dialogue boxes at my intellectual level, allowing me to grasp and understand the content, I’m already struggling from a disadvantaged position. I struggle with querying and don’t have the capacity to submit many manuscripts? I’ve already misplaced.
As my digital endeavors escalated, so did my trepidation: what if this supposed malware turned out to be a genuine threat? The narrative unfolds with a gradual build-up of complexity, driven in part by the whimsical and implausible nature of the plot, which is not dissimilar from those tantalizing emails promising instant wealth transfers from far-flung monarchs seeking a small helping hand to relocate their vast riches. Following this, a star-studded alternative comes into plain sight. Wouldn’t it be a behemoth task for designers to integrate a genuine subpar installer among the numerous fake ones they’ve previously designed? Wouldn’t that be meta?
Although I believe art’s ingenuity lies in effortlessly weaving subtle fictions onto canvases with masterful brushstrokes. As soon as you power up, you take your seat in front of a computer screen, taking on the role of someone immersing themselves in a virtual world. To safeguard this hypothetical computer from potential harm, you would undoubtedly strive your best to ensure its optimal security and integrity. Good luck.
Malware